Update: In November 2019 AWS introduced support for integration between Azure AD and AWS SSO. The integration offers a ton more features, including out of the box support for multiple AWS accounts. I highly recommend you go that route if you’re looking to integrate the two platforms. Check out my series on the new integration here.
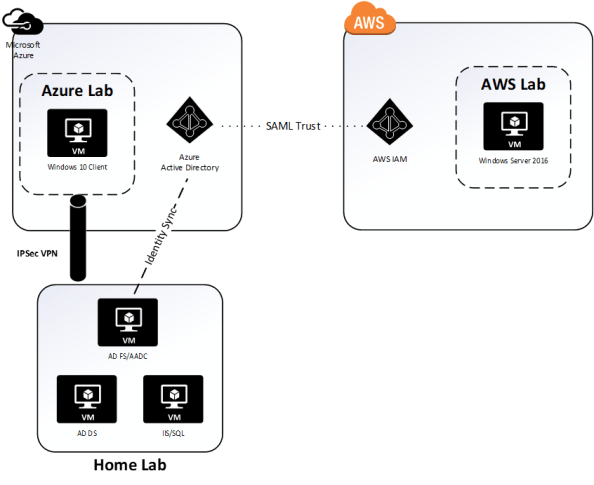
Welcome! This entry continues my series in the integration of Azure AD and AWS. In my first entry I covered what the advantages of the integration are. In the second entry I walked through my lab configuration and went over what happens behind the scenes when an application is added to Azure AD from the application gallery. In this post I’m going to walk through some of the configuration we need to do in both Azure AD and AWS. I’ll also be breaking open the Azure AD and AWS metadata and examining the default assertion sent by Microsoft out of the box.
In my last entry I added the AWS application to my Azure AD tenant from the Azure AD Application Gallery. The application is now shown as added in the All Applications view of the Azure Active Directory blade for my tenant.

After selecting AWS from the listing of applications I’m presented with a variety of configuration options. Starting with Properties we’re provided with some general information and configuration options. We need to ensure that the application is enabled for users to sign-in and that it’s visible to users so we can select it from the access panel later on. Notice also that that I’m configuring the application to require the user be assigned to the application.
On the Users and groups page I’ve assigned Rick Sanchez to the application to allow the account access and display it on the access panel.

After waiting about 10 minutes (there is a delay in the time it takes for the application to appear in the application panel) I log into the Access Panel as Rick Sanchez and we can see that the AWS app has been added for Rick Sanchez.

Back to the properties page of the AWS application, my next stop is the Single sign-on page. Here I drop down the Single Sign-on Mode drop box and select SAML-based Sign-on option. Changing the mode to SAML-based Sign-on exposes a ton of options. The first option that caught my eye was the Amazon Web Services (AWS) Domain and URLs. Take notice of the note that says Amazon Web Services (AWS) is pre-integrated with Azure AD and requires no mandatory URL settings. Yeah, not exactly true as we progress through this series.

Further down we see the section that allows us to configure the unique user identifier and additional attributes. By default Microsoft includes the name, givenName, surName, and emailAddress claims. I’ll need to make some changes there to pass the claims Amazon requires, but let’s hold off on that for now.

Next up a copy of the Azure AD metadata (IdP metadata) is provided for download. Additionally some advanced options are available which provide the capability to sign the SAML response, assertion, or both as well as switching the hash algorithm between SHA1 and SHA256.

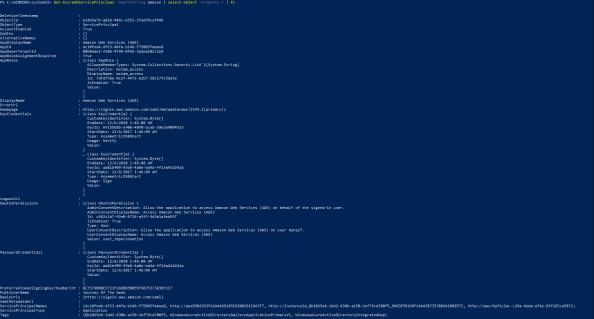
Now like any nerd, I want to poke around the IdP metadata and see what the certificate Azure AD is using to sign looks like. Opening up the metadata in a web browser parses the XML and makes the format look pretty. From there I grab the contents X509Certificate tag (the base-64 encoded public-key certificate), dump it to Notepad, and renam it with a file extension of cer. Low and behold, what do we see but a self-signed certificate. This is a case where I can see the logic that the operational overhead is far greater than the potential security risk. I mean really, does anyone want to deal with the challenge of hundreds of thousands of customers not understanding the basics of public key infrastructure and worrying about revocation, trust chains, and the like? You get a pass Microsoft… This time anyway.

Before I proceed with the next step in the configuration, let’s take a look at what the assertion looks like without any of the necessary configuration. For this I’ll use Fiddler to act as a man-in-the-middle between the client and the web. In session 6 of the screenshot below we see that the SAML response was returned to the web browser from Azure.

Next up we extract that information with the Text Wizard, base-64 decode it, copy it to Notepad, save it as an XML file, and open it with IE. The attributes containing values of interest are as follows:
- Destination – The destination is the service provider assertion consumer URI

- NameID – This is the unique identifier of the used by the service provider to identify the user accessing the service

- Recipient– The recipient attribute references the service the assertion is intended for. Oasis security best practices for SAML require the service provider to verify this attribute match the URI for the service provider assertion consumer URI

- Audience – The audience attribute in the audienceRestriction section mitigates the threat of the assertion being stolen and used to impersonate a user. Oasis security best practices require the service provider to verify this when the assertion is received to ensure it is recognizes the identifier. The way in which this is accomplished is the value in the audience attribute is checked against the service provider EntityID attribute.

Additionally we have some interesting claims including tenantid, objectidentifier of the user object in Azure AD, name, surname, givenname, displayname, identityprovider, and authnmethosreferences. I don’t think any of these need further explanation.

Let’s now take a look at the AWS (service provider in SAML terms) metadata. The AWS metadata is available for download from here. After it’s downloaded it can be opened with IE.

The fields of interest in this set of metadata is:
- EntityID – The entityID is the unique identifier AWS will provide in its authentication requests. Let’s note the value of urn:amazon:webservices for later as it will come in handy due to some issues with Microsoft’s default settings.

- NameIDFormat – This tells me both transient and persistent are accepted. I won’t go into details on Name ID format, you can review that for yourself in the Oasis standard. Suffice to say the Name ID format required by the service provider can throw some wrenches into integrations when using a more basic security token service (STS) like AD FS.

- AssertionConsumerService – This is where our browser will post back the SAML assertion after a successful authentication. Note the URI in the location field.

- RequestedAttributes – This provides us with a listing of all the attributes AWS will accept in an assertion. Note that the only two required attributes are Role and RoleSessionName.
We’ve added the AWS application to Azure AD, granted a user access to the application, and have started the SAML setup within Azure AD (Identity Provider). Let’s continue that setup by configuring which attributes Azure AD will include in the assertions delivered to AWS. From review of the AWS metadata we know that we need to send claims of Role and RoleSessionName. The RoleE will match to an an AWS IAM Role handling authorization of what we can do within AWS and the RoleSessionName provides a unique identifier for the user asserting the entitlement.
Back in the Azure AD Portal I’m going to click the option to View and edit all other user attributes. The exposes the attributes Microsoft sends by default. These include givenName, suName, emailAddress, and name. Since the AWS metadata only requires RoleSessionName and Role, I’m going to delete the other attributes. No sense in exposing additional information that isn’t needed!

After the extra attributes are deleted I create the two required attributes as seen in the screenshot below.

I’m now going to bounce over to the AWS Management Console. After logging in I navigate to the Services menu and choose IAM.

On the IAM menu I choose the Identity providers menu item and hit the Create Provider button.

On the next screen I’m required to configure the identity provider settings. I choose SAML from the drop-down box enter a provider name of MAAD and upload the IdP metadata I downloaded from Azure AD referenced earlier in the blog entry and hit the Next Step button.

On the next page I verify the provider name and the type of identity provider and hit the Create button. Once that is complete I see the new entry listed in identity providers list. Easy right?

We have an identity provider, but that identity provider needs some IAM roles to be associated with the identity provider that my fictional users can assert. For that I go to the Roles section and hit the Create Role button.

On the next screen I select the SAML button as the type of trusted entity since the role is going to be asserted via the SAML trust with Azure AD. Here I select the MAAD provider and choose the option to allow the users to access both the AWS Management Console and the API and then hit the Next: Permissions button.

As I referenced in my first entry to this series, the role I’m going to create is going to be capable of managing all EC2 instances. For that I choose the AmazonEC2FullAccess policy template and then hit the Next:Review button.

On the last screen I name the new role AzureADEC2Admins, write a short description, and hit the Create Role button.

The new role is created and can be seen associated to the identity provider representing the trust between AWS and Azure AD.

Let’s sum up what we did for this entry. We examined the key settings Microsoft exposes for configuration with the AWS integration. We examined the Azure AD (IdP) and AWS (SP) metadata to understand which settings are important to this integration and what those settings do. We examined an assertion generated out of Azure AD prior to any of the necessary customization being completed to understand what a canned assertion looks like. Finally, we completed a majority of the tasks we need to complete on the AWS side to create the SAML trust on the AWS end and to create a role JoG users can asserts. Are your eyes bleeding yet?
In my last post in this series I’ll walk through the rest of the configuration needed on the Azure AD end. This will include going over some of the mistakes the Microsoft tutorial makes as well as covering configuration of Azure AD’s provisioning integration as to what it means and how we can effectively configure it. Finally, we’ll put all the pieces of the puzzle together, assert our identity, and review logs at AWS to see what they look like when a federated user performs actions in AWS.
The journey continues in my fourth entry.